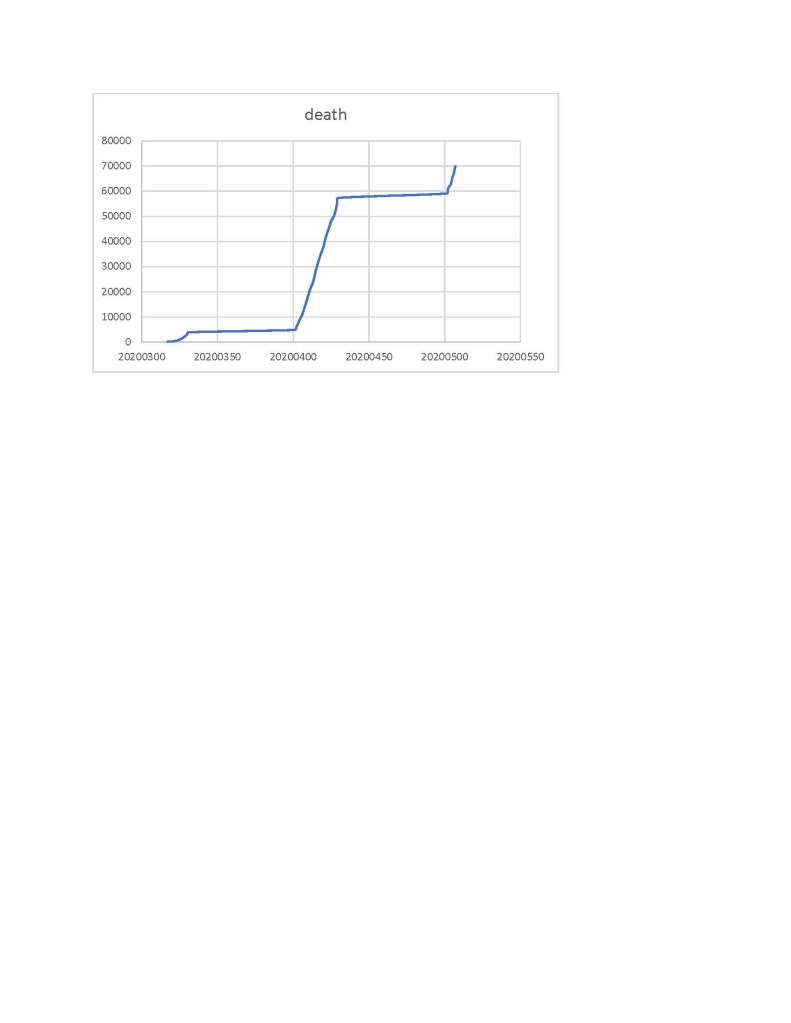
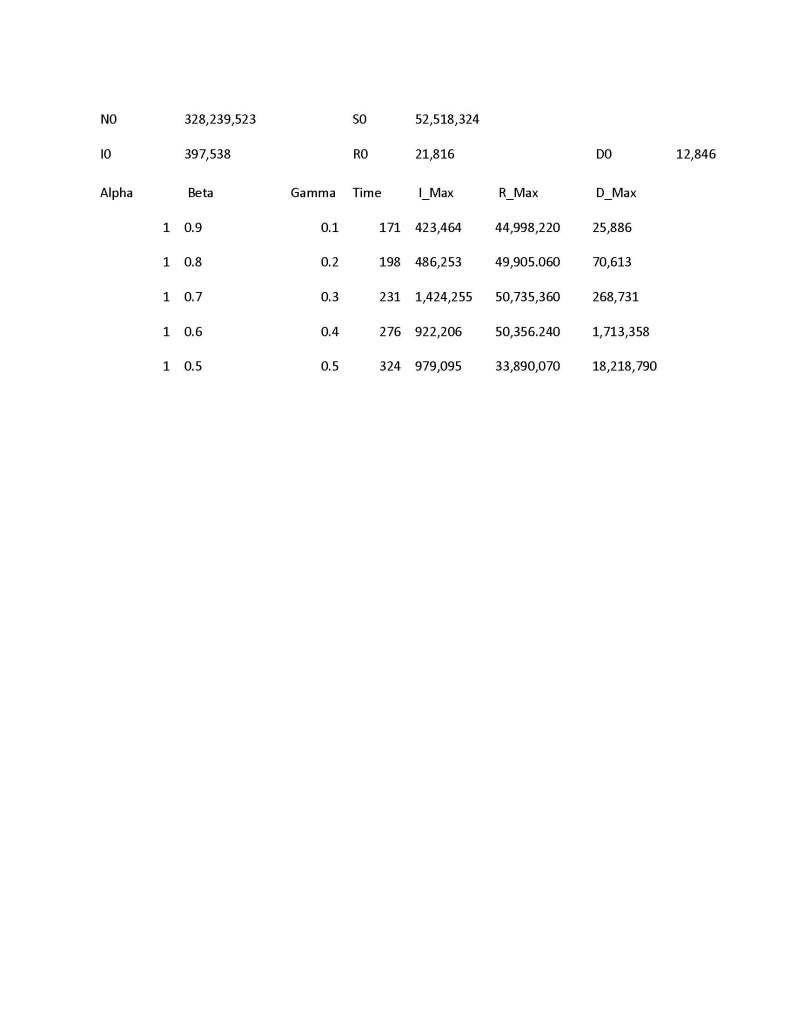
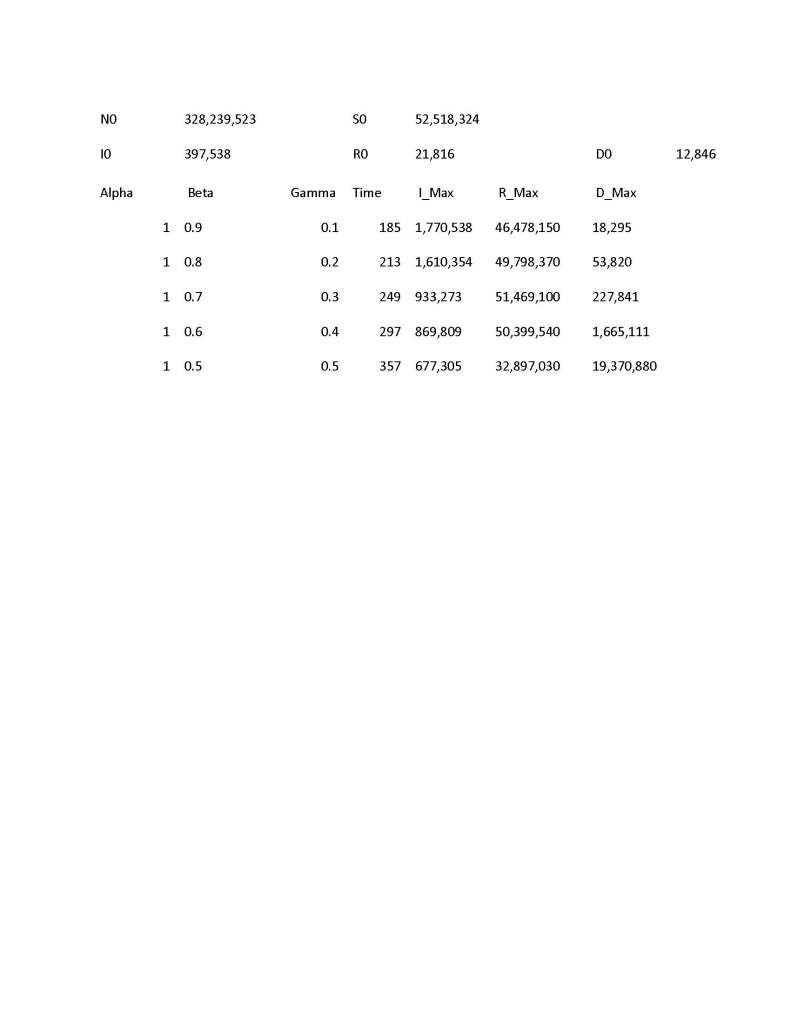
It is doubtful that the Covid-19 plague was intentionally initiated as a weapon of mass destruction aimed at the Western powers. The novel SARS-Corona-19 virus is a positive sense single strand messenger RNA virus and as such it is just too unpredictable and unstable virus that is prone to mutation to be used as an effective and intentional biological weapon. A standard hypothesis is that a glory seeking virologist went into a dawn of time sort of cave seeking viruses which might become the carriers of the next great pandemic and mishandled some mammal vectors. That virologist was probably working with the Wuhan Institute of Virology in China.
Now here is where the accidental unleashing of the Covid-19 plague was fortuitous for a number of states that are very skilled in spreading destructive propaganda and cyber warfare. There are many targets of opportunity in the United states in particular our essential military personnel and politicians. Remember a few nefarious states would love to be able to spread chaos and havoc before our 2020 general elections.
Our country is in a vulnerable state of affairs. A concerted cyber terrorist attack on our delicate and unpredictable financial institutions and banking sector could further devastate the United States. Also security is probably not as efficient in our infrastructure as it was before our current health debacle. Hopefully, the key components of our civil engineering work force and their works (airports, hydroelectric dams, train and road construction, etc.) are being adequately monitored and hardened against computer initiated attacks.