In this first installment of Chapter 9 Hash Functions and Data Integrity of the Handbook, we concentrate on the unkeyed hash functions mentioned in the Chapter which are:
- Matyas-Meyer-Oseas Hash 9.41 Algorithm page 341
- Davies-Meyer Hash 9.42 Algorithm page 341
- Miyaguchi-Preneel Hash 9.43 Algorithm page 341
- MDC-2 (DES Based) 9.46 Algorithm page 342
- MDC-4 (DES Based) 9.47 Algorithm page 343
- MD4 9.49 Algorithm page 346
- MD5 9.51 Algorithm page 347
- SHA-1 (Secure Hash Algorithm 1) 9.53 Algorithm page 348-349
- RIPMD-160 9.55 Algorithm pages 350-351
The first five algorithms are based on the IBM-NIST-NSA encryption algorithm DES (Data Encryption Standard).

Matyas-Meyer-Oseas DES Hash Function abcdefghijklmnopqrstuvwxyz IV = 01ad27b0 75851f2a H1 = 62af6ffa e32867a0 Zbcdefghijklmnopqrstuvwxyz IV = 01ad27b0 75851f2a I1 = 567f7eaf 7420eb6f number of changed bits by a five bits input change = 27 Davies-Meyer DES Hash Function abcdefghijklmnopqrstuvwxyz IV = 464f95ff 30d042d1 H1 = be1c30f4 2f6fc905 Zbcdefghijklmnopqrstuvwxyz IV = 464f95ff 30d042d1 I1 = e56ec4b7 ffd98172 number of changed bits by a five bits input change = 33 Miyaguchi-Preneel DES Hash Function abcdefghijklmnopqrstuvwxyz IV = 164502df 2264bd00 H1 = d866343a 137eee2a Zbcdefghijklmnopqrstuvwxyz IV = 164502df 2264bd00 I1 = becbad0e 0ca8fa64 number of changed bits by a five bits input change = 32

MDC_2 DES Hash Function abcdefghijklmnopqrstuvwxyz G0 = a2a9a035 554856b1 G0T = ed24d012 d536f455 Zbcdefghijklmnopqrstuvwxyz H0 = 5a79b365 970b3216 H0T = 2694dd17 0d93ddb1 number of changed bits by a five bits input change = 55 MDC-4 DES Hash Function abcdefghijklmnopqrstuvwxyz IV = 3cd408f2 528789b6 IVT = 0ac7b125 5a8a8729 G0 = 80140bb0 e49cc013 G0T = 80140bb0 e49cc013 Zbcdefghijklmnopqrstuvwxyz IV = 3cd408f2 528789b6 IVT = 0ac7b125 5a8a8729 H0 = 37d40179 ce50bcc9 H0T = 37d40179 ce50bcc9 number of changed bits by a five bits input change = 62
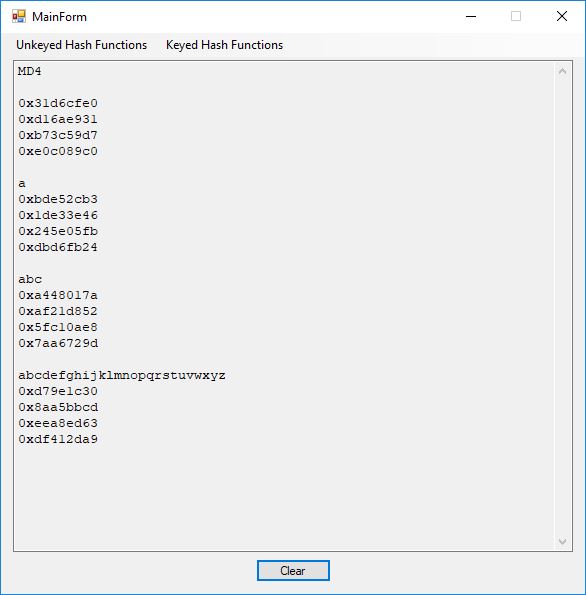
MD4 0x31d6cfe0 0xd16ae931 0xb73c59d7 0xe0c089c0 a 0xbde52cb3 0x1de33e46 0x245e05fb 0xdbd6fb24 abc 0xa448017a 0xaf21d852 0x5fc10ae8 0x7aa6729d abcdefghijklmnopqrstuvwxyz 0xd79e1c30 0x8aa5bbcd 0xeea8ed63 0xdf412da9

MD5 0xd41d8cd9 0x8f00b204 0xe9800998 0xecf8427e a 0x0cc175b9 0xc0f1b6a8 0x31c399e2 0x69772661 abc 0x90015098 0x3cd24fb0 0xd6963f7d 0x28e17f72 abcdefghijklmnopqrstuvwxyz 0xc3fcd3d7 0x6192e400 0x7dfb496c 0xca67e13b
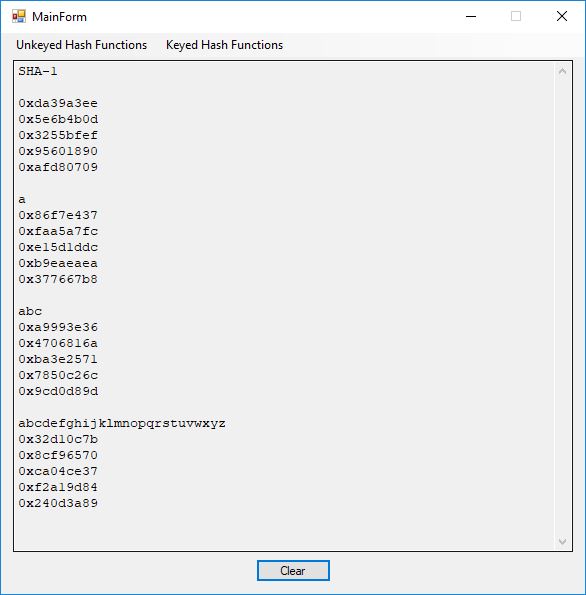
SHA-1 0xda39a3ee 0x5e6b4b0d 0x3255bfef 0x95601890 0xafd80709 a 0x86f7e437 0xfaa5a7fc 0xe15d1ddc 0xb9eaeaea 0x377667b8 abc 0xa9993e36 0x4706816a 0xba3e2571 0x7850c26c 0x9cd0d89d abcdefghijklmnopqrstuvwxyz 0x32d10c7b 0x8cf96570 0xca04ce37 0xf2a19d84 0x240d3a89

RIPEMD-160 0x9c1185a5 0xc5e9fc54 0x61280897 0x7ee8f548 0xb2258d31 a 0x0bdc9d2d 0x256b3ee9 0xdaae347b 0xe6f4dc83 0x5a467ffe abc 0x8eb208f7 0xe05d987a 0x9b044a8e 0x98c6b087 0xf15a0bfc abcdefghijklmnopqrstuvwxyz 0xf71c2710 0x9c692c1b 0x56bbdceb 0x5b9d2865 0xb3708dbc
Test vectors for MD4, MD5, SHA-1, and RIPEMD-160 can be found in Table 9.6 of the Handbook on page 345.