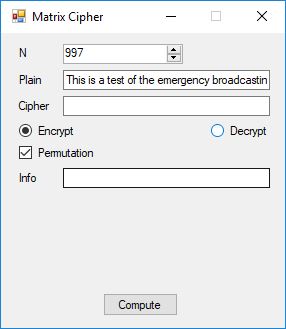
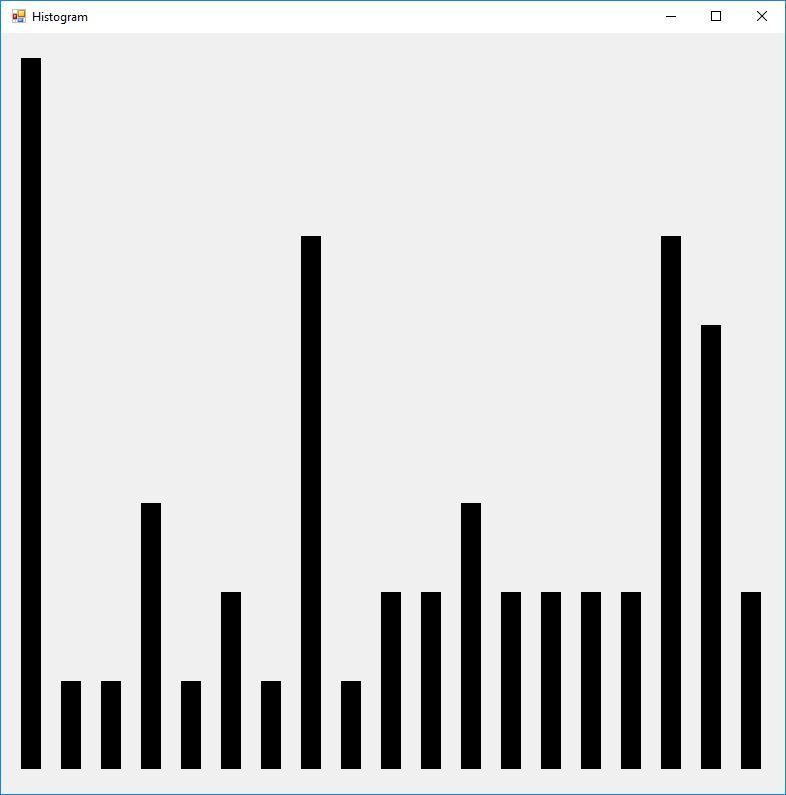
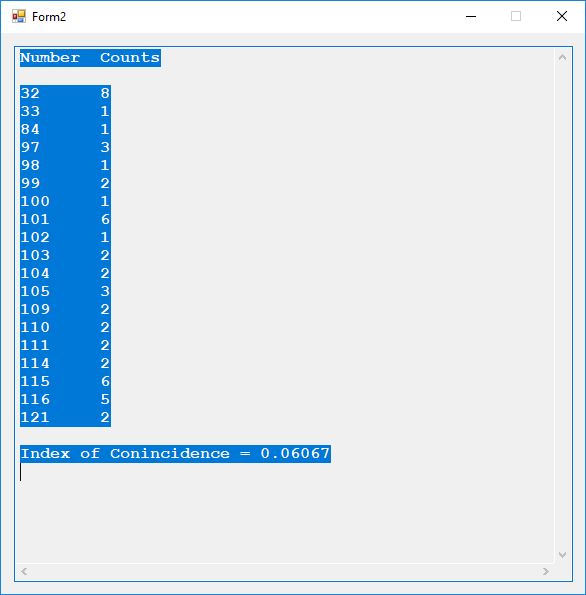
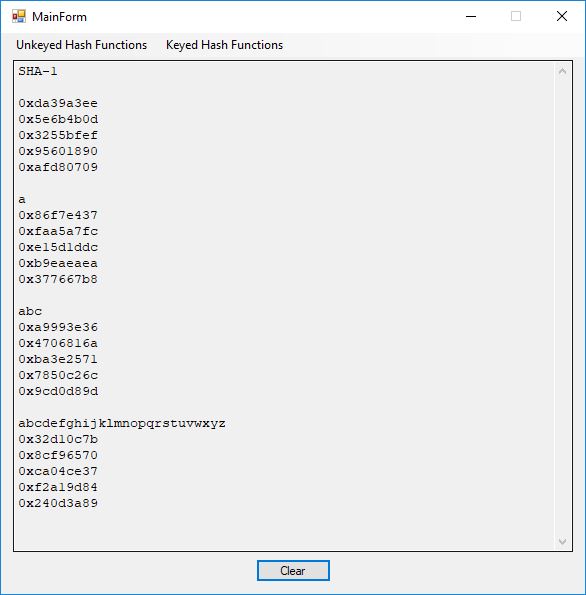
From a software engineer and computer scientist’s point of view, the key sections on block ciphers in this chapter of the Handbook are 7.4 DES, 7.5 FEAL, 7.6 IDEA, and 7.7 SAFER, RC5, … My original C implementations are probably from the era 1996 to 1998 of my life. In January and February of 2017 I translated the C code to C#. The results below are from the test application. I added some code on the triple-DES algorithm.
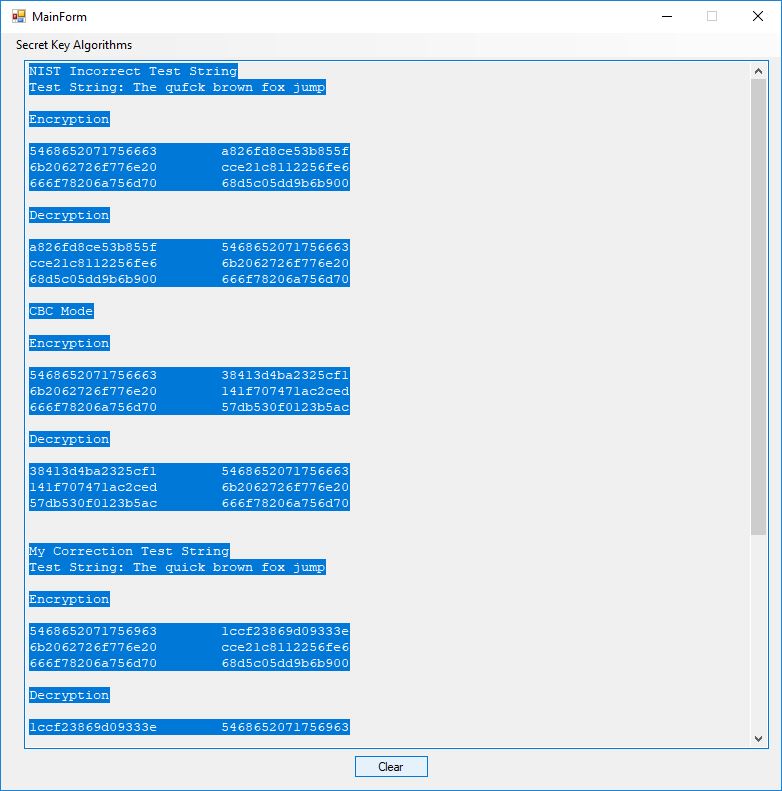
Here are the numbers from the triple DES test.
NIST Incorrect Test String
Test String: The qufck brown fox jump
Encryption
5468652071756663 a826fd8ce53b855f
6b2062726f776e20 cce21c8112256fe6
666f78206a756d70 68d5c05dd9b6b900
Decryption
a826fd8ce53b855f 5468652071756663
cce21c8112256fe6 6b2062726f776e20
68d5c05dd9b6b900 666f78206a756d70
CBC Mode
Encryption
5468652071756663 38413d4ba2325cf1
6b2062726f776e20 141f707471ac2ced
666f78206a756d70 57db530f0123b5ac
Decryption
38413d4ba2325cf1 5468652071756663
141f707471ac2ced 6b2062726f776e20
57db530f0123b5ac 666f78206a756d70
My Correction Test String
Test String: The quick brown fox jump
Encryption
5468652071756963 1ccf23869d09333e
6b2062726f776e20 cce21c8112256fe6
666f78206a756d70 68d5c05dd9b6b900
Decryption
1ccf23869d09333e 5468652071756963
cce21c8112256fe6 6b2062726f776e20
68d5c05dd9b6b900 666f78206a756d70
CBC Mode
Encryption
5468652071756963 5ba523a59a510971
6b2062726f776e20 0da06400f058192a
666f78206a756d70 743dc4df1c592655
Decryption
5ba523a59a510971 5468652071756963
0da06400f058192a 6b2062726f776e20
743dc4df1c592655 666f78206a756d70
The DES test output is illustrated as follows:
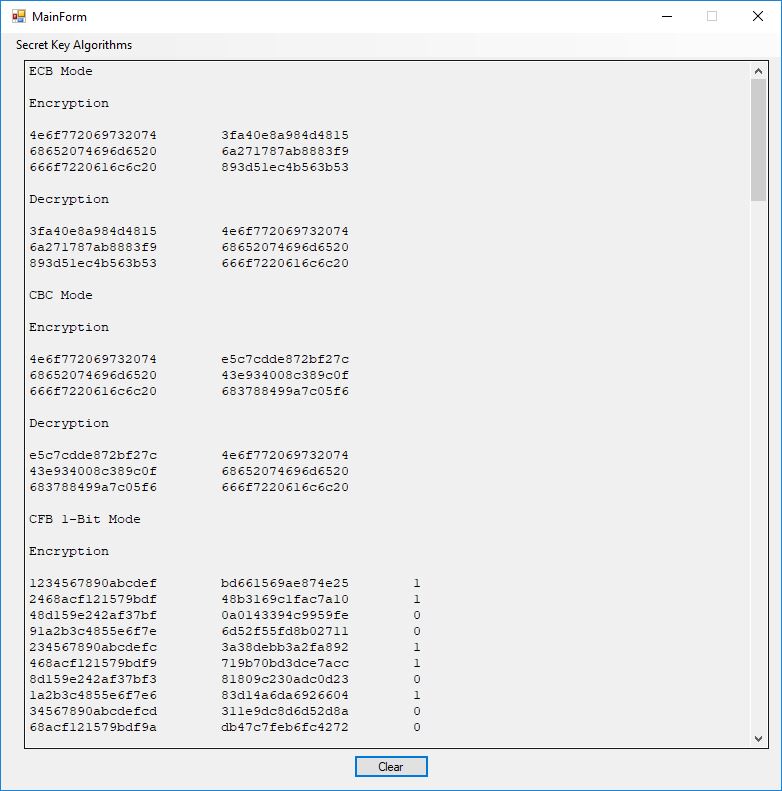
All of the numbers from DES (Date Encryption Standard) test are given below:
ECB Mode
Encryption
4e6f772069732074 3fa40e8a984d4815
68652074696d6520 6a271787ab8883f9
666f7220616c6c20 893d51ec4b563b53
Decryption
3fa40e8a984d4815 4e6f772069732074
6a271787ab8883f9 68652074696d6520
893d51ec4b563b53 666f7220616c6c20
CBC Mode
Encryption
4e6f772069732074 e5c7cdde872bf27c
68652074696d6520 43e934008c389c0f
666f7220616c6c20 683788499a7c05f6
Decryption
e5c7cdde872bf27c 4e6f772069732074
43e934008c389c0f 68652074696d6520
683788499a7c05f6 666f7220616c6c20
CFB 1-Bit Mode
Encryption
1234567890abcdef bd661569ae874e25 1
2468acf121579bdf 48b3169c1fac7a10 1
48d159e242af37bf 0a0143394c9959fe 0
91a2b3c4855e6f7e 6d52f55fd8b02711 0
234567890abcdefc 3a38debb3a2fa892 1
468acf121579bdf9 719b70bd3dce7acc 1
8d159e242af37bf3 81809c230adc0d23 0
1a2b3c4855e6f7e6 83d14a6da6926604 1
34567890abcdefcd 311e9dc8d6d52d8a 0
68acf121579bdf9a db47c7feb6fc4272 0
d159e242af37bf34 b73850afa3b8ed89 0
a2b3c4855e6f7e68 f5fb19dd00590800 1
4567890abcdefcd1 0f4351a9bbffe5a5 1
8acf121579bdf9a3 769593c58e20d41b 1
159e242af37bf347 0e949d3f3a293d64 1
2b3c4855e6f7e68f 921eb7ffeacd0db9 0
567890abcdefcd1e d2ad109c8895fb95 1
acf121579bdf9a3d 3c36317828a9bd04 1
59e242af37bf347b e7248586e7e4ecac 0
b3c4855e6f7e68f6 f9a58e16a7597c5e 0
67890abcdefcd1ec e939fdf63d177946 1
cf121579bdf9a3d9 f325eac046bad58d 0
9e242af37bf347b2 8385a6d975ffdbba 0
3c4855e6f7e68f64 70a54baceae7ba6b 1
Decryption
1234567890abcdef bd661569ae874e25 0
2468acf121579bdf 48b3169c1fac7a10 1
48d159e242af37bf 0a0143394c9959fe 0
91a2b3c4855e6f7e 6d52f55fd8b02711 0
234567890abcdefc 3a38debb3a2fa892 1
468acf121579bdf9 719b70bd3dce7acc 1
8d159e242af37bf3 81809c230adc0d23 1
1a2b3c4855e6f7e6 83d14a6da6926604 0
34567890abcdefcd 311e9dc8d6d52d8a 0
68acf121579bdf9a db47c7feb6fc4272 1
d159e242af37bf34 b73850afa3b8ed89 1
a2b3c4855e6f7e68 f5fb19dd00590800 0
4567890abcdefcd1 0f4351a9bbffe5a5 1
8acf121579bdf9a3 769593c58e20d41b 1
159e242af37bf347 0e949d3f3a293d64 1
2b3c4855e6f7e68f 921eb7ffeacd0db9 1
567890abcdefcd1e d2ad109c8895fb95 0
acf121579bdf9a3d 3c36317828a9bd04 1
59e242af37bf347b e7248586e7e4ecac 1
b3c4855e6f7e68f6 f9a58e16a7597c5e 1
67890abcdefcd1ec e939fdf63d177946 0
cf121579bdf9a3d9 f325eac046bad58d 1
9e242af37bf347b2 8385a6d975ffdbba 1
3c4855e6f7e68f64 70a54baceae7ba6b 1
CFB 8-Bit Mode
Encryption
1234567890abcdef bd661569ae874e25 f3
34567890abcdeff3 7039546f9a0f6330 1f
567890abcdeff31f ad1b78b0bb371be7 da
7890abcdeff31fda 27350b01d5ca31f7 07
90abcdeff31fda07 68863426e397685d 01
abcdeff31fda0701 6798240e8c6b685f 14
cdeff31fda070114 421feefb3f8ca64f 62
eff31fda07011462 9a169a9b50666575 ee
f31fda07011462ee 703b1799be9a5748 18
1fda07011462ee18 1a4aee195be70077 7f
Decryption
1234567890abcdef bd661569ae874e25 4e
34567890abcdeff3 7039546f9a0f6330 6f
567890abcdeff31f ad1b78b0bb371be7 77
7890abcdeff31fda 27350b01d5ca31f7 20
90abcdeff31fda07 68863426e397685d 69
abcdeff31fda0701 6798240e8c6b685f 73
cdeff31fda070114 421feefb3f8ca64f 20
eff31fda07011462 9a169a9b50666575 74
f31fda07011462ee 703b1799be9a5748 68
1fda07011462ee18 1a4aee195be70077 65
CFB 64-Bit Mode
Encryption
1234567890abcdef bd661569ae874e25 f3096249c7f46e51
f3096249c7f46e51 cefba3ef73ff92a4 a69e839b1a92f784
a69e839b1a92f784 65290313e8e2ca02 03467133898ea622
Decryption
1234567890abcdef bd661569ae874e25 4e6f772069732074
f3096249c7f46e51 cefba3ef73ff92a4 68652074696d6520
a69e839b1a92f784 65290313e8e2ca02 666f7220616c6c20
OFB ISO 10116 64-Bit Mode
Encryption
1234567890abcdef bd661569ae874e25 f3096249c7f46e51
bd661569ae874e25 5d976a504786581f 35f24a242eeb3d3f
5d976a504786581f 5b0229c3443694e3 3d6d5be3255af8c3
Decryption
1234567890abcdef bd661569ae874e25 4e6f772069732074
bd661569ae874e25 5d976a504786581f 68652074696d6520
5d976a504786581f 5b0229c3443694e3 666f7220616c6c20
OFB FIPS-81 1-Bit Mode
Encryption
1234567890abcdef bd661569ae874e25 1
2468acf121579bdf 48b3169c1fac7a10 1
48d159e242af37be 8879ea93c63d77a5 1
91a2b3c4855e6f7d 0d36e16101e86d61 0
234567890abcdefa e9eab8cfc00f4ac3 0
468acf121579bdf5 9d41640f97df7904 0
8d159e242af37beb 32f72fd1899eda45 1
1a2b3c4855e6f7d6 ca2a095d20f4e769 1
34567890abcdefad de869588355e1041 1
68acf121579bdf5b 11245e6a8720ddce 1
d159e242af37beb6 836b0be324094a97 0
a2b3c4855e6f7d6d c07714703b296a5a 1
4567890abcdefadb bf6380ecc196d599 0
8acf121579bdf5b7 96ed6856969aef13 0
159e242af37beb6f 3823feaa3d170085 1
2b3c4855e6f7d6de 2d57dc0c899d6700 1
567890abcdefadbc 2fe1c261c0e1a302 0
acf121579bdf5b78 778ad641faa047d0 1
59e242af37beb6f0 f66ae4359eec3755 0
b3c4855e6f7d6de1 cd0bda27e32a13da 0
67890abcdefadbc3 9f71f74488551801 1
cf121579bdf5b787 a62e89aa6b85be74 0
9e242af37beb6f0f 7b0b2e1de987b804 1
3c4855e6f7d6de1e 7f41b5ef07c3ea29 1
Decryption
1234567890abcdef bd661569ae874e25 0
2468acf121579bdf 48b3169c1fac7a10 1
48d159e242af37be 8879ea93c63d77a5 0
91a2b3c4855e6f7d 0d36e16101e86d61 0
234567890abcdefa e9eab8cfc00f4ac3 1
468acf121579bdf5 9d41640f97df7904 1
8d159e242af37beb 32f72fd1899eda45 1
1a2b3c4855e6f7d6 ca2a095d20f4e769 0
34567890abcdefad de869588355e1041 0
68acf121579bdf5b 11245e6a8720ddce 1
d159e242af37beb6 836b0be324094a97 1
a2b3c4855e6f7d6d c07714703b296a5a 0
4567890abcdefadb bf6380ecc196d599 1
8acf121579bdf5b7 96ed6856969aef13 1
159e242af37beb6f 3823feaa3d170085 1
2b3c4855e6f7d6de 2d57dc0c899d6700 1
567890abcdefadbc 2fe1c261c0e1a302 0
acf121579bdf5b78 778ad641faa047d0 1
59e242af37beb6f0 f66ae4359eec3755 1
b3c4855e6f7d6de1 cd0bda27e32a13da 1
67890abcdefadbc3 9f71f74488551801 0
cf121579bdf5b787 a62e89aa6b85be74 1
9e242af37beb6f0f 7b0b2e1de987b804 1
3c4855e6f7d6de1e 7f41b5ef07c3ea29 1
OFB 8-Bit FIPS-81 Mode
Encryption
1234567890abcdef bd661569ae874e25 f3
34567890abcdefbd 25e73b5d4cbd2359 4a
567890abcdefbd25 5f970070553623d0 28
7890abcdefbd255f 704ad48bf9eec8fa 50
90abcdefbd255f70 a0b1a091bb787553 c9
abcdefbd255f70a0 b58127681139ee7f c6
cdefbd255f70a0b5 694d556ef5806a65 49
efbd255f70a0b569 f1885324299132a2 85
bd255f70a0b569f1 be639ff6d7b74b04 d6
255f70a0b569f1be e17b6ae22b4bad65 84
Decryption
1234567890abcdef bd661569ae874e25 4e
34567890abcdefbd 25e73b5d4cbd2359 6f
567890abcdefbd25 5f970070553623d0 77
7890abcdefbd255f 704ad48bf9eec8fa 20
90abcdefbd255f70 a0b1a091bb787553 69
abcdefbd255f70a0 b58127681139ee7f 73
cdefbd255f70a0b5 694d556ef5806a65 20
efbd255f70a0b569 f1885324299132a2 74
bd255f70a0b569f1 be639ff6d7b74b04 68
255f70a0b569f1be e17b6ae22b4bad65 65
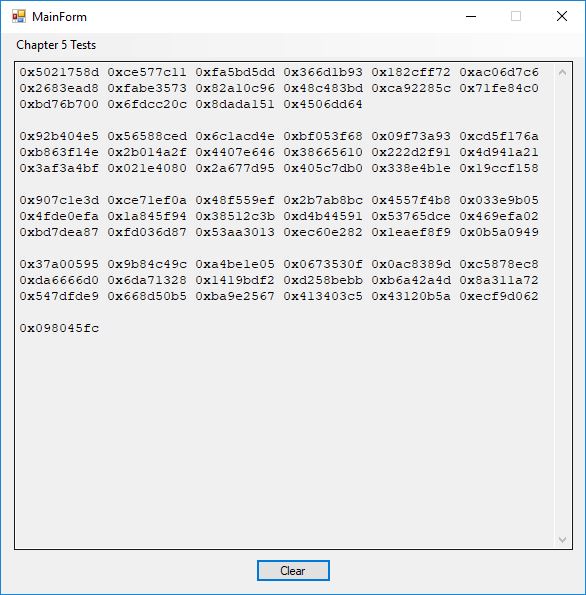
The results of Section 7.5 FEAL (Fast Data Encipherment Algorithm) in particular 7.99 Example page 262 are shown below:

Here are the numbers of the 7.99 Example copied from the preceding application’s text box:
0xDF3B
0xCA36
0xF17C
0x1AEC
0x45A5
0xB9C7
0x26EB
0xAD25
0x8B2A
0xECB7
0xAC50
0x9D4C
0x22CD
0x479B
0xA8D5
0x0CB5
0xCEEF2C86 0xF2490752
0x00000000 0x00000000
Moving on to Section 7.6 IDEA (International Data Encryption Algorithm) a 64-bit block cipher:

Again for clarity we reproduce the preceding numbers below see Table 7.12 page 265 and Table 7.13 page 266\:
1 0x0001 0x0002 0x0003 0x0004 0x0005 0x0006 0x00F0 0x00F5 0x010A 0x0105
2 0x0007 0x0008 0x0400 0x0600 0x0800 0x0A00 0x222F 0x21B5 0xF45E 0xE959
3 0x0C00 0x0E00 0x1000 0x0200 0x0010 0x0014 0x0F86 0x39BE 0x8EE8 0x1173
4 0x0018 0x001C 0x0020 0x0004 0x0008 0x000C 0x57DF 0xAC58 0xC65B 0xBA4D
5 0x2800 0x3000 0x3800 0x4000 0x0800 0x1000 0x8E81 0xBA9C 0xF77F 0x3A4A
6 0x1800 0x2000 0x0070 0x0080 0x0010 0x0020 0x6942 0x9409 0xE21B 0x1C64
7 0x0030 0x0040 0x0050 0x0060 0x0000 0x2000 0x99D0 0xC7F6 0x5331 0x620E
8 0x4000 0x6000 0x8000 0xA000 0xC000 0xE001 0xD98D 0xD331 0xD002 0x754C
9 0x0080 0x00C0 0x0100 0x0140 0x0000 0x0000 0xC614 0xD0C2 0xD431 0x9E6E
1 0xFE01 0xFF40 0xFF00 0x659A 0xC000 0xE001 0x0000 0xD331 0xD002 0x754C
2 0xFFFD 0x8000 0xA000 0xCCCC 0x0000 0x2000 0x0ECF 0x7ECD 0xCDFF 0x3475
3 0xA556 0xFFB0 0xFFC0 0x52AB 0x0010 0x0020 0x68EA 0xFFAF 0xD82A 0xD560
4 0x554B 0xFF90 0xE000 0xFE01 0x0800 0x1000 0x531C 0xA0AC 0x6FD6 0x90E9
5 0x332D 0xC800 0xD000 0xFFFD 0x0008 0x000C 0x3E10 0x1E89 0x4E8A 0x2626
6 0x4AAB 0xFFE0 0xFFE4 0xC001 0x0010 0x0014 0x11F2 0x5D0A 0xFC89 0x6B6A
7 0xAA96 0xF000 0xF200 0xFF81 0x0800 0x0A00 0x8177 0x4429 0xD97C 0xDF40
8 0x4925 0xFC00 0xFFF8 0x552B 0x0005 0x0006 0x35AB 0x6CE9 0x33CF 0x069D
9 0x0001 0xFFFE 0xFFFD 0xC001 0x0000 0x0000 0x35AB 0x33CD 0x6CE6 0xC1A8
Finally the results from Section 7.7 on SAFER, RC5, etc.
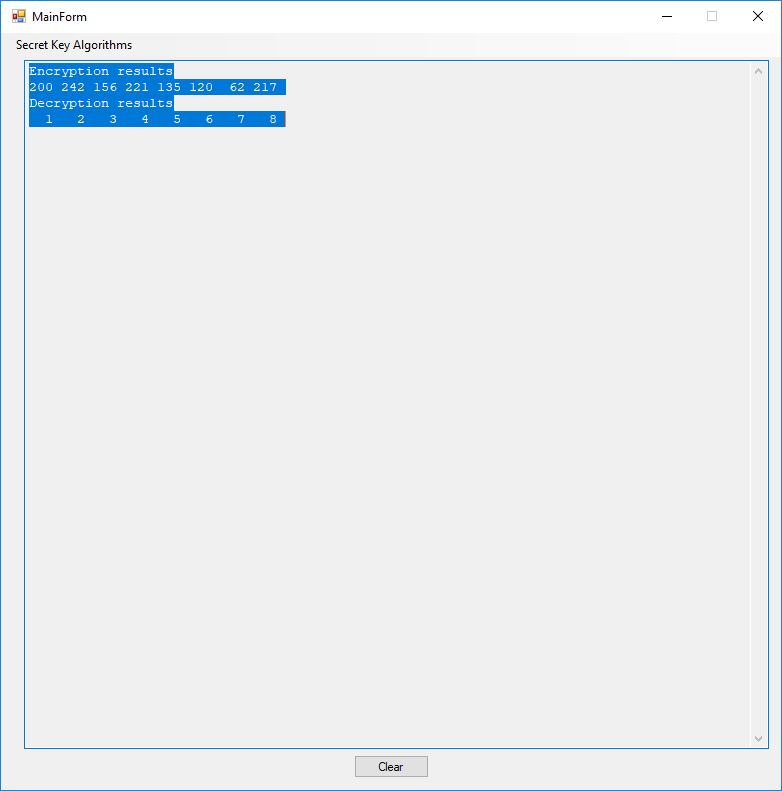
See 7.114 Example page 269.
Encryption results
200 242 156 221 135 120 62 217
Decryption results
1 2 3 4 5 6 7 8
RC5 application results:

See 7.118 Example page 270:
0x15E444EB 0x249831DA
0xB278C165 0xCC97D18